By involving the general public, as many as 14 million clicks to suspicious websites were avoided in 2022. This equates to about 25 alerts to internet users per minute. If you know that Belgium has a population of 12 million, you understand that these are huge numbers. This is the result of the Centre for Cybersecurity Belgium's Belgium Anti-Phishing Shield (BAPS), which alerts internet users to unsafe websites. This system is unique in Europe.
The CCB has been counting on the general public's cooperation for years to report suspicious messages. Every day, we receive thousands of suspicious emails. In 2022, 6 million messages were forwarded to suspicious@safeonweb.be. From these messages, we were able to detect no less than 665,000 suspicious URLs. The success of the email address suspicious@safeonweb.be is still growing: in 2023, we are receiving an average of up to 30,000 suspicious messages a day.
We forward the suspicious URLs from these emails to Google SafeBrowsing and Microsoft SmartScreen. Browsers use this information to alert visitors to malicious websites. As we have no control over how quickly Google and Microsoft then proceed to block links, the CCB, together with the internet service providers Belnet, Proximus, Telenet and Orange, has successfully developed its own system and procedure to alert internet users in real time, called the Belgium Anti-Phishing Shield (BAPS).
BAPS is unique in Europe. The CCB has already had several opportunities to share this project with partner organizations all over Europe. This practice may therefore be rolled out in other countries in the near future.
The Centre for Cybersecurity Belgium asks everyone to forward suspicious messages to suspcious@safeonweb.be. The faster the messages can be handled, the fewer victims there will be. Less observant internet users who then click on a suspicious link will land on a warning page. BAPS is only possible thanks to the public's forwarding of these suspicious messages.
Internet users can also send images of fake text messages and forward messages with QR codes. Our technology can detect URLs in images and QR codes.
This is a great example of constructive cooperation between the general public and the government and is unique in Europe. It shows that our country can do a lot despite its limited resources. By fighting cybercrime together, we will be able to greatly reduce it in the coming years. There is still much work to be done, but we must not give up.
Miguel De Bruycker, general director, Centre for Cybersecurity Belgium

What is the Belgium Anti-Phishing Shield or BAPS?
The Belgium Anti-Phishing Shield (BAPS) alerts the public based on malicious links that are sent to the CCB via suspicious@safeonweb.be. BAPS was tested and progressively launched in 2021. Today it has been almost fully rolled out.
When an internet user in Belgium clicks on a link, the request to retrieve this internet page is sent to their internet service provider (ISP). Thanks to BAPS, the ISP's server compares the requested internet domain (website) with a list of entirely malicious domains. If the requested URL appears on this list, the ISP's server will redirect the user to a warning page.
Where does the list of malicious websites come from?
We compile the list of malicious websites thanks to the thousands of suspicious messages people forward to us every day at suspicious@safeonweb.be. The internet domains appearing in these messages are automatically analysed and forwarded to the internet service providers very quickly: the quicker this happens, the more effective the system is. Thanks to a thorough evaluation, no genuine websites are listed by mistake and BAPS only works against phishing. To avoid complaints about the system, we always make sure that no legitimate sites are blocked. Only when websites are marked as completely "dangerous" do they appear on the list.
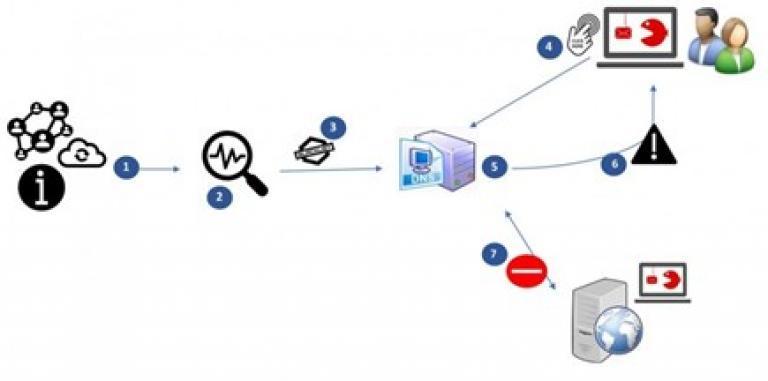
How does BAPS work?
- The CCB receives information about possible malicious websites through suspicious@safeonweb.be and other channels;
- An analysis of potentially malicious websites is performed, and those that are malicious are then placed on a list;
- The list of malicious websites is forwarded to internet service providers;
- An internet user clicks on a malicious URL;
- The ISP compares the DNS request with the list of malicious websites (domains);
- If this leads to a malicious website, the internet user is "redirected" to a warning page;
- The internet user does not visit the malicious website.