NIS2, Are you in scope?
Belgium's new cybersecurity law entered into force.
Find out what the NIS2 legislation means for your organization, if you could be in scope and what your obligations may be.
You couldn't find the answer to your question on this page? Check out our FAQ!
The Law of 26 April 2024 establishing a framework for the cybersecurity of networks and information systems of general interest for public security (the "NIS2 Law") transposes Directive (EU) 2022/2555 of the European Parliament and of the Council of 14 December 2022 (the "NIS2 Directive") in Belgium. It will enter into force on 18th October 2024.
The NIS2 law updates the Belgian legal framework on cybersecurity by superseding the law of 7th April 2019 establishing a framework for the security of networks and information systems of general interest for public security (NIS1 law). The new text is accompanied by the Royal Decree from 9th June 2024 which executes its provisions, for example by designating the Centre for Cybersecurity Belgium (CCB) as the national cybersecurity authority.
Networks and information systems have become central elements of our society. However, the number, scale, sophistication, frequency and impact of incidents involving these networks and information systems now pose considerable threats to the population, businesses and public authorities.
The aim of the law is to strengthen cybersecurity measures, incident management and the supervision of entities providing services that are essential for maintaining critical societal or economic activities. It also aims to improve the coordination of public policies in the area of cybersecurity.

To be covered by the Belgian NIS2 law, an organisation must in principle:
These criteria are explained in the following sections.
In addition to the explanations on this page, you can also do our scope test:
Before analysing the law itself, it is important to first verify two eventualities that have an impact of how the NIS2 scope applies to an organisation.
First, it is important to note that the NIS2 law automatically applies to all entities identified as critical entities (formerly "operators of critical infrastructure") in the sense of the law of 19 December 2025 on the resilience of critical entities, regardless of their size. Under the NIS2 law these entities are essential entities.
Critical entities are organisations formally identified by the competent sectoral authority pursuant to the law of 19 December 2019. Organisations that have been identified have received a formal letter for their identification and are subject to specific security obligations.
Critical entities ("CER entities") have replaced "operators of critical infrastructure". The latter will automatically be considered as critical entities after the 17th July 2026 pursuant to article 79 of the law of 19 December 2025.
Second, entities identified as operators of essential services (OES) or digital service providers (DSP) under the NIS1 law shall in principle also fall under the NIS2 law if they exceed the necessary size thresholds (see section 1). The reason for this is simple: the scope of the NIS2 directive is an extension of the scope of the NIS1 directive.
To fall into the scope of the NIS2 law, an organisation must be of a certain size. In principle, an organisation must at least be a medium-sized enterprise, calculated using the annex of Commission Recommendation 2003/361/EC, but there are certain exceptions (more on these below).
The size of an organisation is established using two criteria: staff headcount (measured in full-time equivalents (FTE)*) and financial amounts (annual turnover and/or annual balance sheet total). How exactly these two criteria are established can be found in the annex of the Recommendation itself or in the Commission’s handy user guide to the SME definition.
To determine the size of an organisation, one must first look at the staff headcount:
Afterwards, the staff headcount must be combined with the financial amounts to receive the definitive categorisation: an enterprise may choose to meet either the turnover or the balance sheet total ceiling. It may exceed one of the financial ceilings without impact on its SME status. We thus only look at the lowest of the two amounts.
The ceilings for annual turnover are the following:
The ceilings for annual balance sheet total are the following:
Example 1: an enterprise with 35 FTE* (small) has an annual turnover of 1.000.000€ (small) and an annual balance sheet total of 50.000.000€ (large). For the financial amounts, it choses to only look at the lowest: its turnover. Thus, it’s a small or micro enterprise.
Example 2: an enterprise with 80 FTE* (medium) has an annual turnover of 1.000.000€ (small) and an annual balance sheet total of 70.000.000€ (large). For the financial amounts, it choses to only look at the lowest: its turnover. Because the turnover is small but the staff headcount is medium, it’s a medium-sized enterprise.
Visually, it looks like this:

If we combine the different possible sizes with the service criterion, we get the following scope of application (with some exceptions - see below):
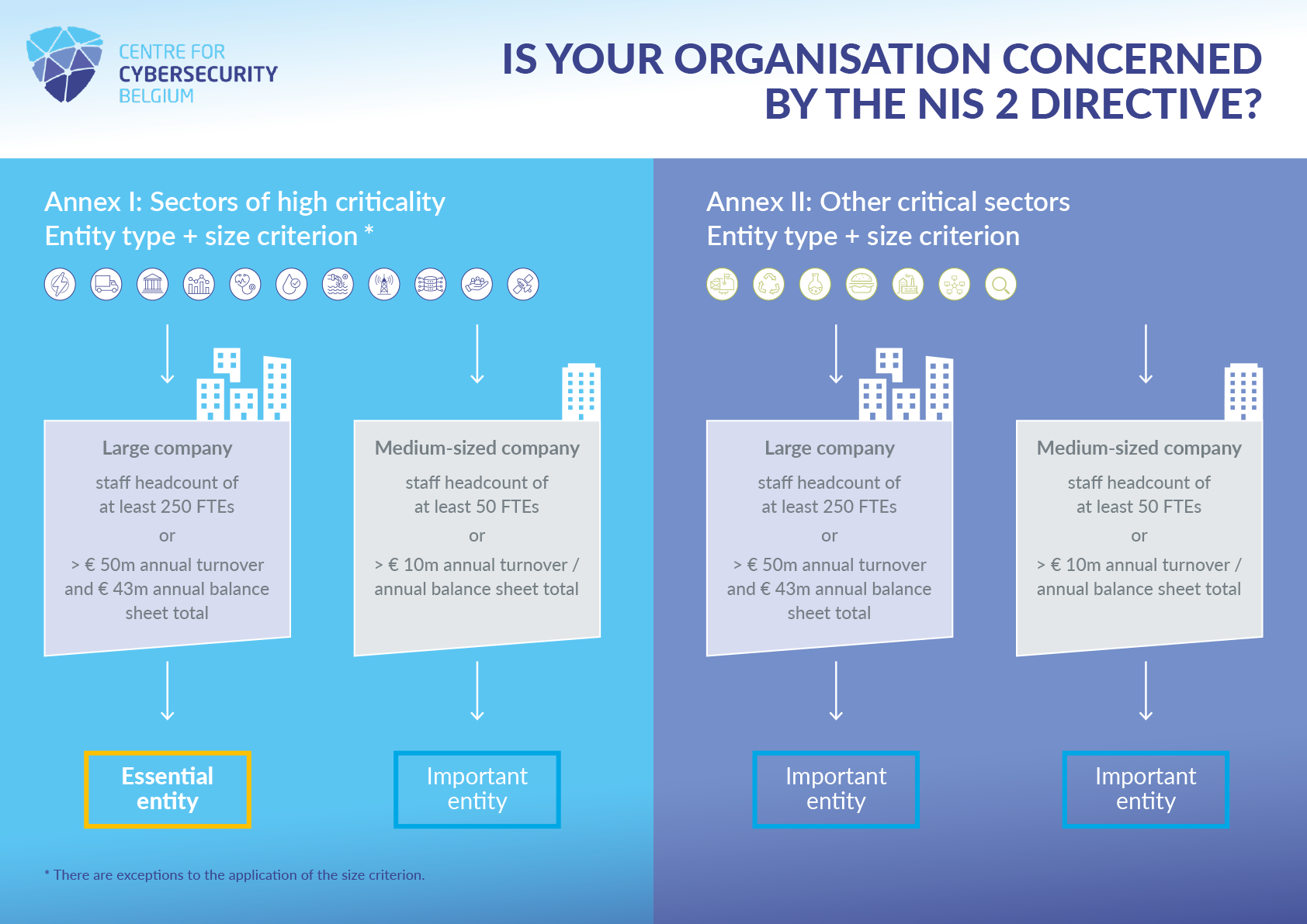
* Full-time equivalents (FTE) (called “annual work units (AWU)” in the Recommendation) are the number of persons who worked full-time within the enterprise in question or on its behalf during the entire reference year under consideration. The work of persons who have not worked the full year, the work of those who have worked part-time, regardless of duration, and the work of seasonal workers are counted as fractions of AWU. The Recommendation and the guide further detail which staff members have to be counted.
The difference between essential and important entities mainly relates to how strictly they are supervised and sanctioned.
It is important to note that the Recommendation also stipulates that the calculation of the size of an organisation that is part of a group (so-called “partner enterprises” or “linked enterprises”) implies a consolidation of the data of the different components of this group. Further details on this subject can be found in the Recommendation or in the guide.
There are nevertheless a number of exceptions to the size-cap. Certain types of entities fall into the scope of application of the NIS2 law, regardless of their size:
Independently of these rules, the national cybersecurity authority (the CCB) will also be able to specifically identify entities as "essential" or "important", for example where they are the sole provider of a service or where the disruption of the service provided could have a significant impact on public security, public safety or public health.
Beyond the size-cap, The service condition requires an organisation to fully analyse every single of its services provided, by sector and sub-sector, to third parties. This is important, given that even the most ancillary service provided may make an organisation as a whole fall into the scope of the NIS2 law, except when stated otherwise in the definition of said service.
All services falling under the NIS2 law are detailed in annexes I and II (or in the definitions) of the law. If an organisation provides one of the services mentioned there and fulfils the corresponding size criterion, then it falls into the scope of the NIS2 law if it can be linked to Belgium (see section 3).
The different services are grouped together by sectors. Here is the list of the different sectors and sub-sectors:
| Highly critical sectors (annex I) | Other critical sectors (annex II) |
|---|---|
|
|
Most services are defined in reference to definitions found in EU legislative instruments. It is of very high importance to consult these definitions to verify if they correspond to the actual service provided by an organisation. To help organisations with this task, the CCB created an Excel table that compiles all these definitions together in one single document:
An organisation analysing whether it falls into the scope of the NIS2 law thus has to make the link between a service it provides and a service mentioned in the annexes of the law. It should be noted that it is possible that an organisation covers multiple services and falls into multiple sectors.
For a better overview of the scope of the law, we invite you to consult our visual summary of the scope:
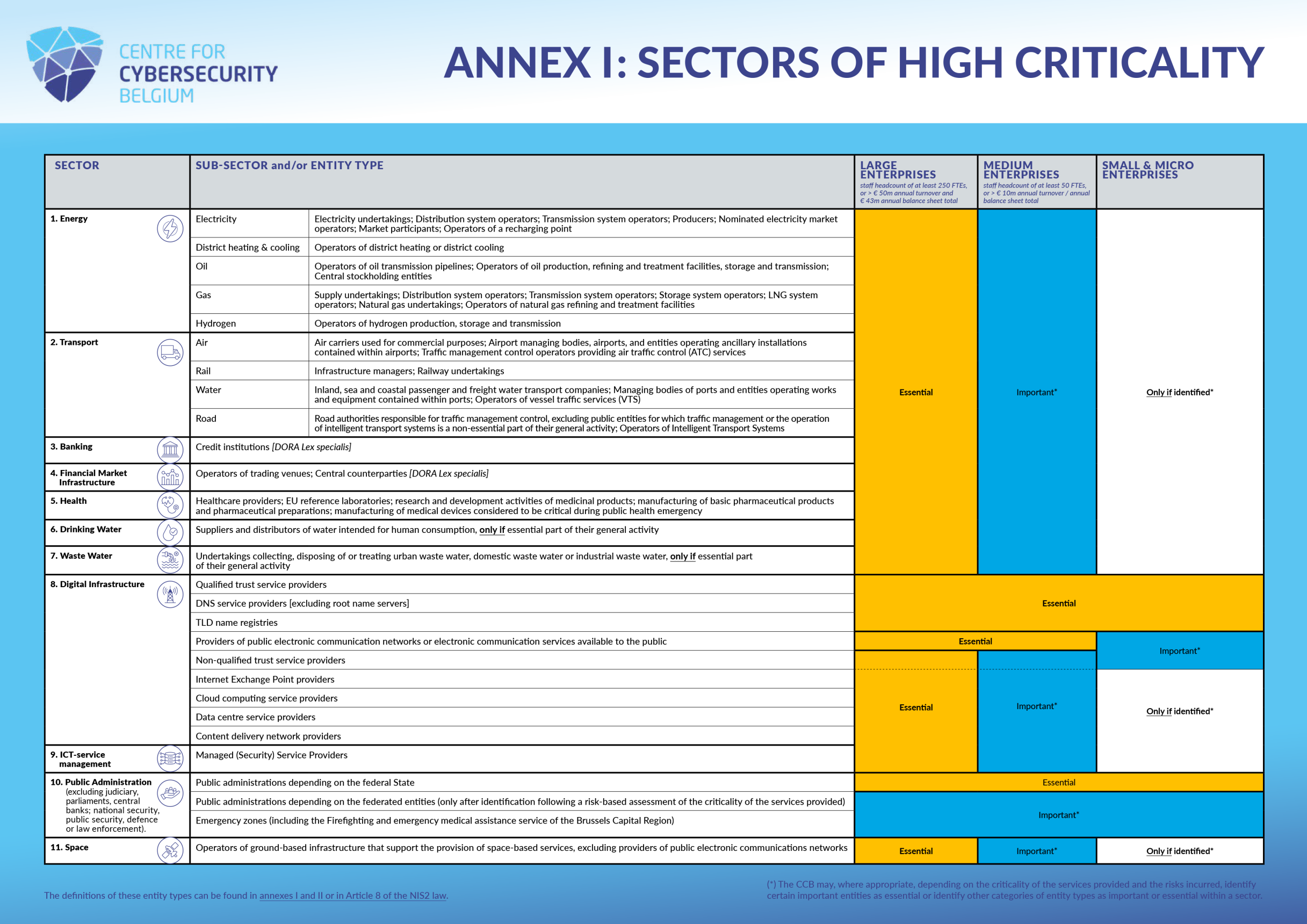
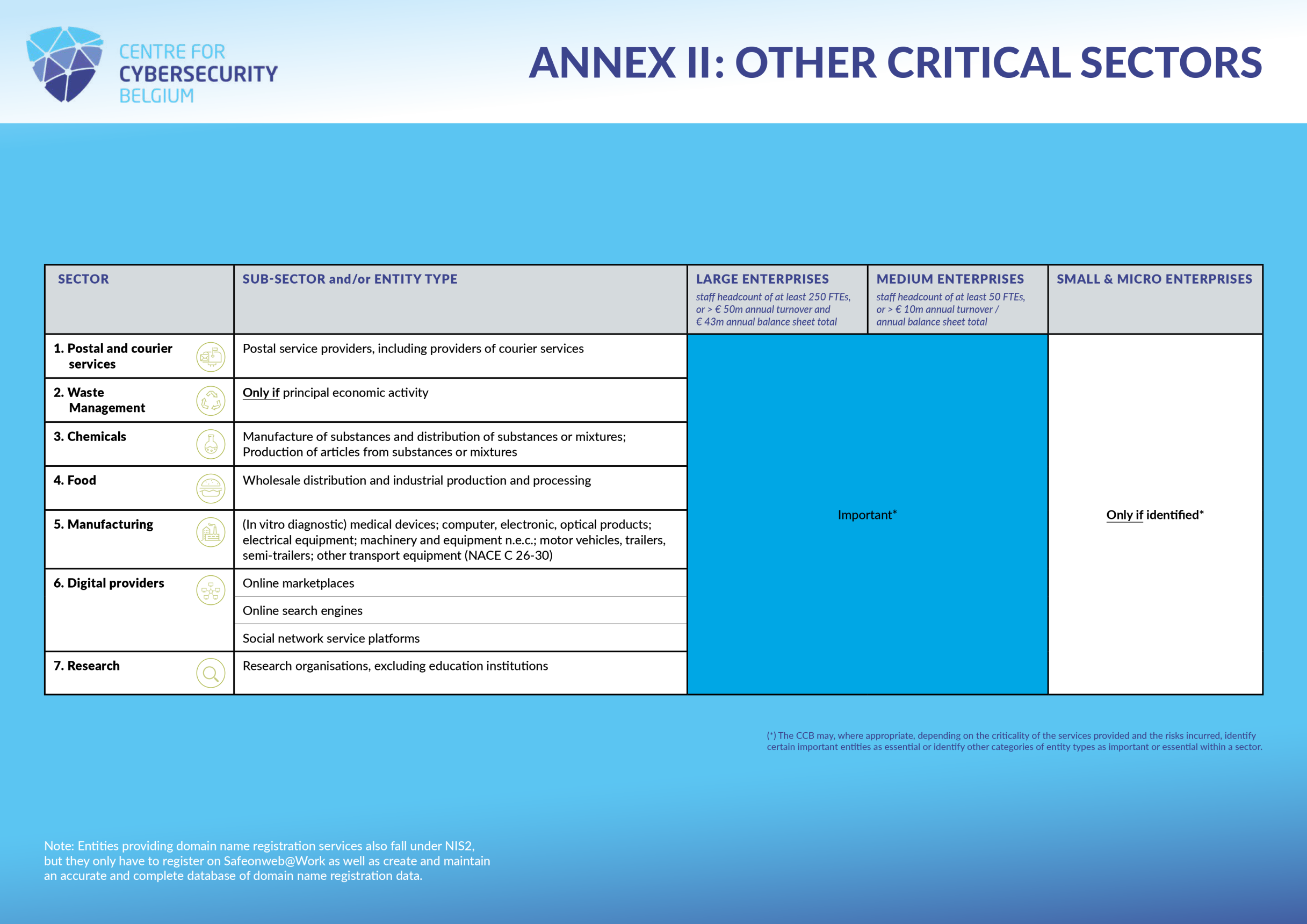
In principle, the Belgian NIS2 law only applies to entities established in Belgium that provide their services or carry out their activities within the EU. Two concepts are important here:
However, there are three exceptions to the rule of establishment in Belgium:
The concept of “main establishment” refers to the establishment where the decisions related to the cybersecurity risk-management measures are predominantly taken. If this cannot be determined or if such decisions are not taken in the Union, the main establishment shall be the establishment where the entity carries out cybersecurity operations. If this place can again not be determined, then the main establishment is where the entity has the highest number of employees in the Union.
* If an entity referred to in point 2) is not established in the EU but provides its services there, it must appoint a legal representative who is established in a Member State where it provides its services. If this representative is located in Belgium, the entity will be considered as having its main establishment in Belgium.
If an entity has several establishments in different EU Member States, it will be subject to the transposition laws in each of the Member States concerned. The various competent national authorities will work together regarding inspections and the notification of significant incidents.
It is possible that after a throughout analysis of the scope of application of the NIS2 law, certain organisations realise that they do, in fact, not fall under said law. All non-NIS2 organisations should be aware that the NIS2 law can still affect them in two ways.
First, the national cybersecurity authority (the CCB) can identify certain organisations, regardless of their size, as essential or important entities under the NIS2 law in four different circumstances:
This process unfolds in concertation with the concerned entity and other related actors, such as the sectoral authority (if it exists) and the relevant federated entities. More information on this procedure can be found in article 11 of the NIS2 law or in our FAQ.
Second, an organisation may fall into the supply chain of a NIS2 entity and be faced with the obligation to implement cybersecurity risk-management measures because of a contractual requirement. NIS2 entities indeed have the obligation to insure the security of their supply chain, including security-related aspects concerning the relationships between each entity and its direct suppliers or service providers.
In this context, the Centre for Cybersecurity Belgium advises all organisations that may find themselves in the supply chain of a NIS2 entity, to at least comply with the measures set out in the CyberFundamentals (CyFun®) Framework level Basic. A NIS2 entity could theoretically impose the compliance with a certain CyFun® level onto its direct suppliers or service providers.
The NIS2 law imposes a number of obligations on essential and important entities. These include registration on Safeonweb@Work, implementation of cybersecurity risk-management measures, notification of significant incidents to the national CSIRT (the CCB), obligations for management and cooperation with the authorities.
All of these obligations will be detailed in the subsequent sections.
Complementary information can be found in our FAQ.
NIS2 entities falling into the scope of the Belgian NIS2 law have to register their organisation at the CCB. In practice, this registration takes the shape of an online from, to be completed here on Safeonweb@Work.
The deadline for registration depends on the type of entity. In principle, essential and important entities, as well as domain name registration service providers, have 5 months from the entry into force of the law to register. With the entry into force scheduled for 18th October 2024, registration must be completed by 18th March 2025 at the latest.
When registering, companies must provide the following information:
For entities that have already provided this information to a NIS2 sectoral authority, the information only needs to be updated where necessary. If the information changes, all entities must inform the CCB immediately.
There is a slightly adapted regime for the following types of entities from the digital sectors:
They must register within 2 months of the law entering into force, i.e. by 18th December 2024 at the latest, and provide the following information:
Here again, every entity is required to inform the CCB immediately of any changes to their information.
In practice, some of this information is obtained directly from the Crossroads Bank for Enterprises (CBE) during the registration process.
Essential and important entities must take appropriate and proportionate technical, operational and organisational measures to manage the risks to the security of the networks and information systems which they use in the course of their activities or in the provision of their services. These measures must eliminate or reduce the impact of incidents on the recipients of their services and on other services.
In addition, the measures implemented have to ensure a level of security for networks and information systems that is appropriate to the existing risk, taking into account the state of the art and, where relevant, applicable European and international standards, as well as the cost of implementation. In assessing the proportionality of these measures, due account should be taken of the degree of exposure of the entity to risk, the size of the concerned entity, as well as the likelihood of incidents occurring and their severity, including societal and economic consequences.
Thus, the measures should be as well adapted as possible to the concrete situation of the concerned entity.
The NIS2 law also states that these measures are based on an "all-hazards" approach and aim to protect network and information systems and their physical environment against incidents. The law lists 11 minimum measures that every NIS2 entity must implement:
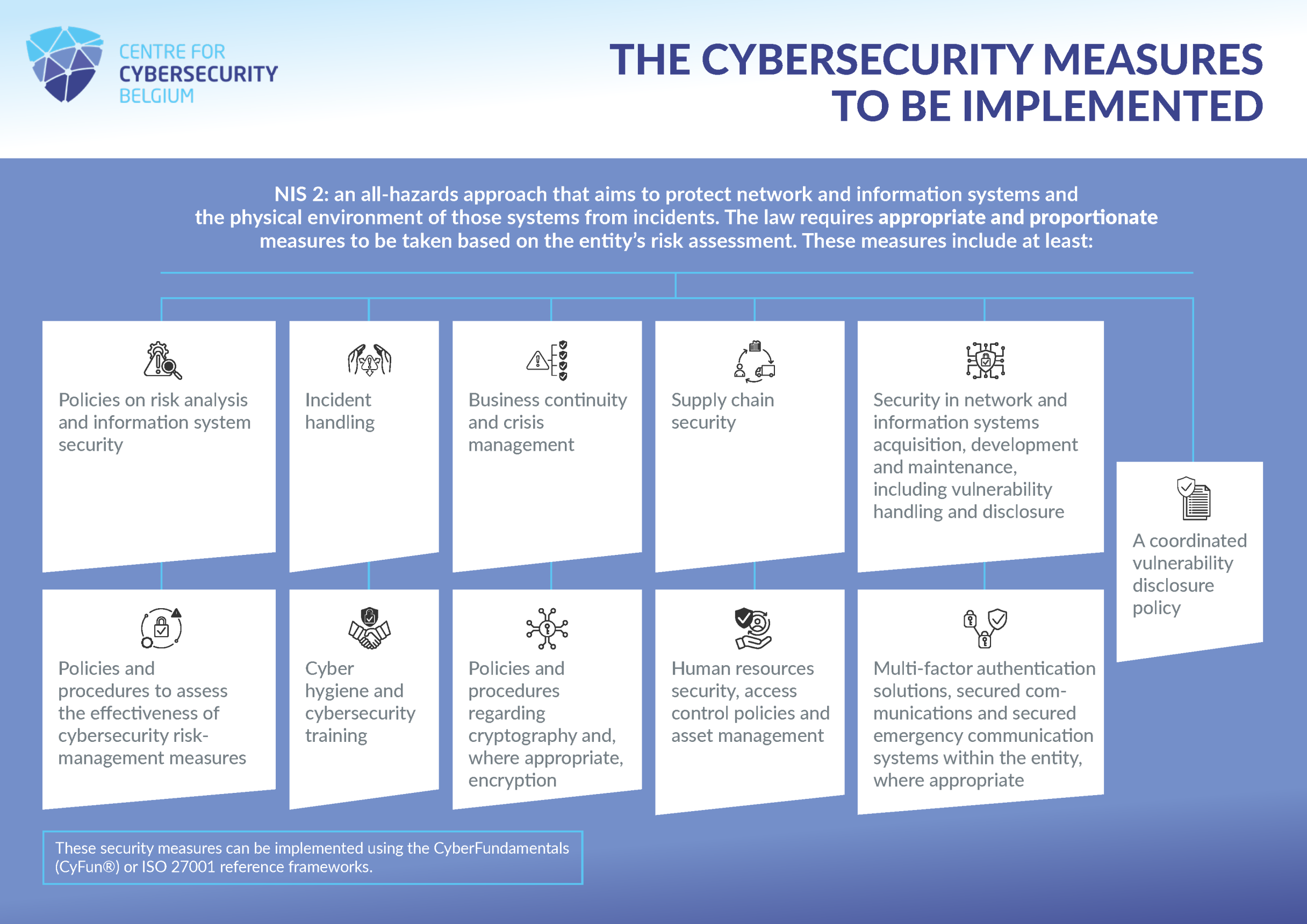
 | To facilitate the practical implementation of these measures, the Centre for Cybersecurity Belgium advises all NIS2 entities to make use of the CyberFundamentals (CyFun®) Framework, which covers all these points. A validated implementation of the CyFun Framework allows NIS2 entities to benefit from a presumption of conformity. For more information, visit our CyFun Website and see our chapter on supervision below. |
For DNS service providers, TLD name registries, cloud computing service providers, data centre service providers, content delivery network providers, managed service providers, managed security service providers, providers of online market places, of online search engines and of social networking services platforms, and trust service providers, the European commission has adopted Implementing regulation 2024/2690 which details the technical and the methodological requirements of the 11 minimum cybersecurity measures referred to in NIS2. In June 2025, ENISA published the “NIS2 Technical Implementation Guidance” to support these entities in the implementation of the cybersecurity measures from the implementing regulation.
The NIS2 law stipulates that essential and important entities must notify the national CSIRT (the CCB) of any significant incident affecting the provision of their services in the (sub-)sectors listed in the annexes of the law, including, where appropriate, information that makes it possible to determine whether the incident in question has a cross-border impact.
In order to fulfil this obligation, one must understand what is meant by “incident” and by “significant”.
The NIS2 law defines “incident” as an event compromising the availability, authenticity, integrity or confidentiality of stored, transmitted or processed data or of the services offered by, or accessible via, network and information systems.
A “significant” incident is any incident which has a significant impact on the provision of services in the sectors or subsectors listed in the annexes of the NIS2 law, and which
If the incident in question fits this definition, then the notification shall be made to the national CSIRT (the CCB) in several stages:
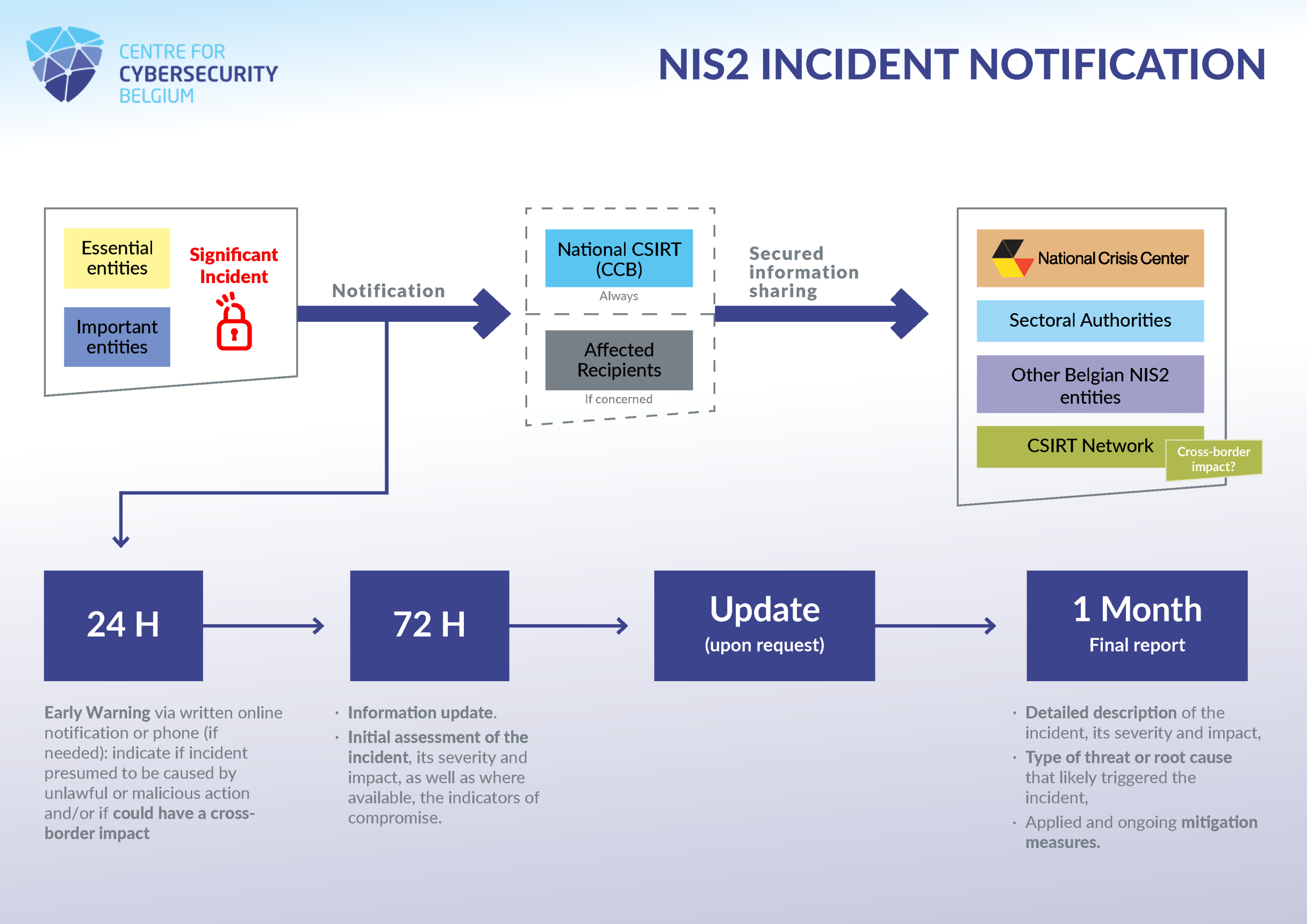
In practice, notification will be made through our notification platform. More information can be found in our notification guide.
Access the notification platform
On top of the notification to the national CSIRT, where appropriate, the concerned entities shall inform the recipients of their services of the significant incidents that may affect the provision of the services from annexes I and II provided to them. The entities shall also inform the recipients of their services that may be affected by a significant cyberthreat of said threat and of all the measures and corrections that may be taken to respond to it.
For DNS service providers, TLD name registries, cloud computing service providers, data centre service providers, content delivery network providers, managed service providers, managed security service providers, providers of online market places, of online search engines and of social networking services platforms, and trust service providers, the European commission has adopted Implementing regulation 2024/2690 which details the specific the criteria for assessing if an incident is considered as “significant”. For the entities concerned by the implementing act, these specific rules apply. In the event of contradiction between the CCB notification guide and the provisions of the implementing act, the latter shall prevail for these entities.
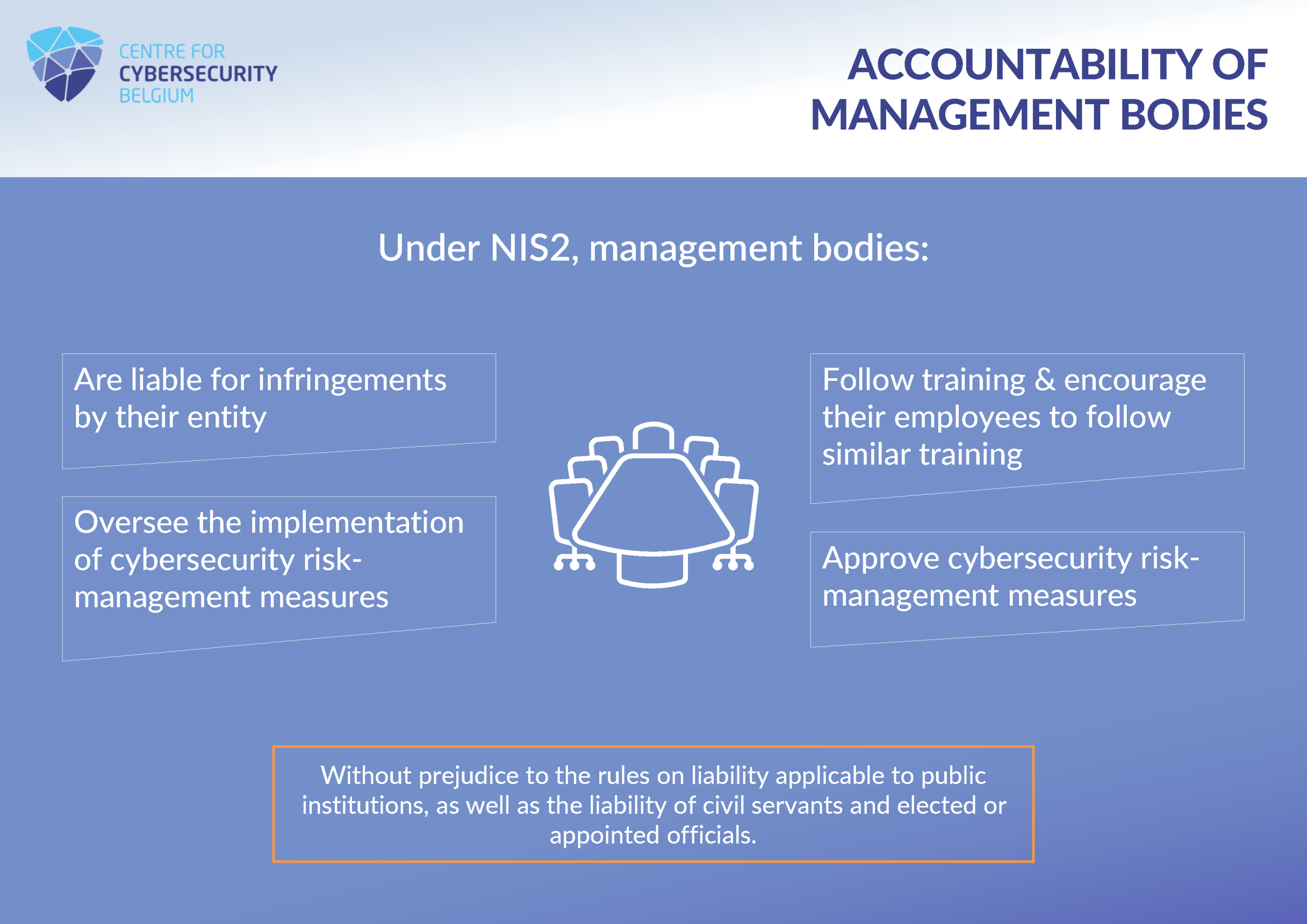
The management bodies of NIS2 entities must approve cybersecurity risk management measures and oversee their implementation. If the entity breaches its obligations with regard to risk management measures, the management body is liable.
Members of the management bodies are obliged to follow training to ensure that their knowledge and skills are sufficient to identify risks and assess cybersecurity risk-management practices and their impact on the services provided by the entity concerned.
The explanatory memorandum of the NIS2 law defines “member of a management body” as:
Any natural or legal person who :
Where the entity in question is a company governed by Belgian law, this control is determined in accordance with articles 1:14 to 1:18 of the Companies and Associations Code. Where the person whose role is being examined is a legal person, the concept of "member of a management body" is examined recursively and covers both the legal person in question and any member of a management body of that legal person. |
The responsible persons and/or legal representatives of an entity must have the power to ensure that the entity complies with the law. They are liable for their failure to do so.
The liability of management bodies, responsible persons and legal representatives is without prejudice to the rules on liability applicable to public institutions, as well as the liability of civil servants and elected or appointed officials.
The NIS2 law requires entities falling within its scope to cooperate with the national authorities responsible for its implementation, in particular the CCB and the sectoral authorities.
This cooperation generally takes the form of an exchange of information on the security of networks and information systems, but also includes cooperation between the entity and the CCB's or the sectoral inspection service.
When we talk about supervision under the NIS2 law, we need to distinguish between two categories of entities: essential entities and important entities. The main difference between the two relates to supervision and sanctions:
This section will goes into detail on how the supervision will play out, which deadlines entities have to respect and what sanctions could be imposed.
More information about the CyberFundamentals Framework is available on its dedicated website.
Essential entities must undergo a mandatory regular conformity assessment. This assessment is carried out on the basis of a choice made by the entity between three options:
The list of authorised CABs is available here: https://atwork.safeonweb.be/open-media/1101/download?inline.
The conformity assessment statement that essential entities receive after the conformity assessment of their chosen framework, allows them to benefit from a presumption of conformity. Until proven otherwise, they are presumed to have respected their obligations.
Because of the proactive and reactive supervision of essential entities, the inspection service may also inspect them at any time. For important entities, supervision is only carried out "ex post" by the inspection service. In principle, therefore, they are not subject to regular conformity assessment. However, these entities may voluntarily submit to the same regime as essential entities and as such also receive a presumption of conformity.
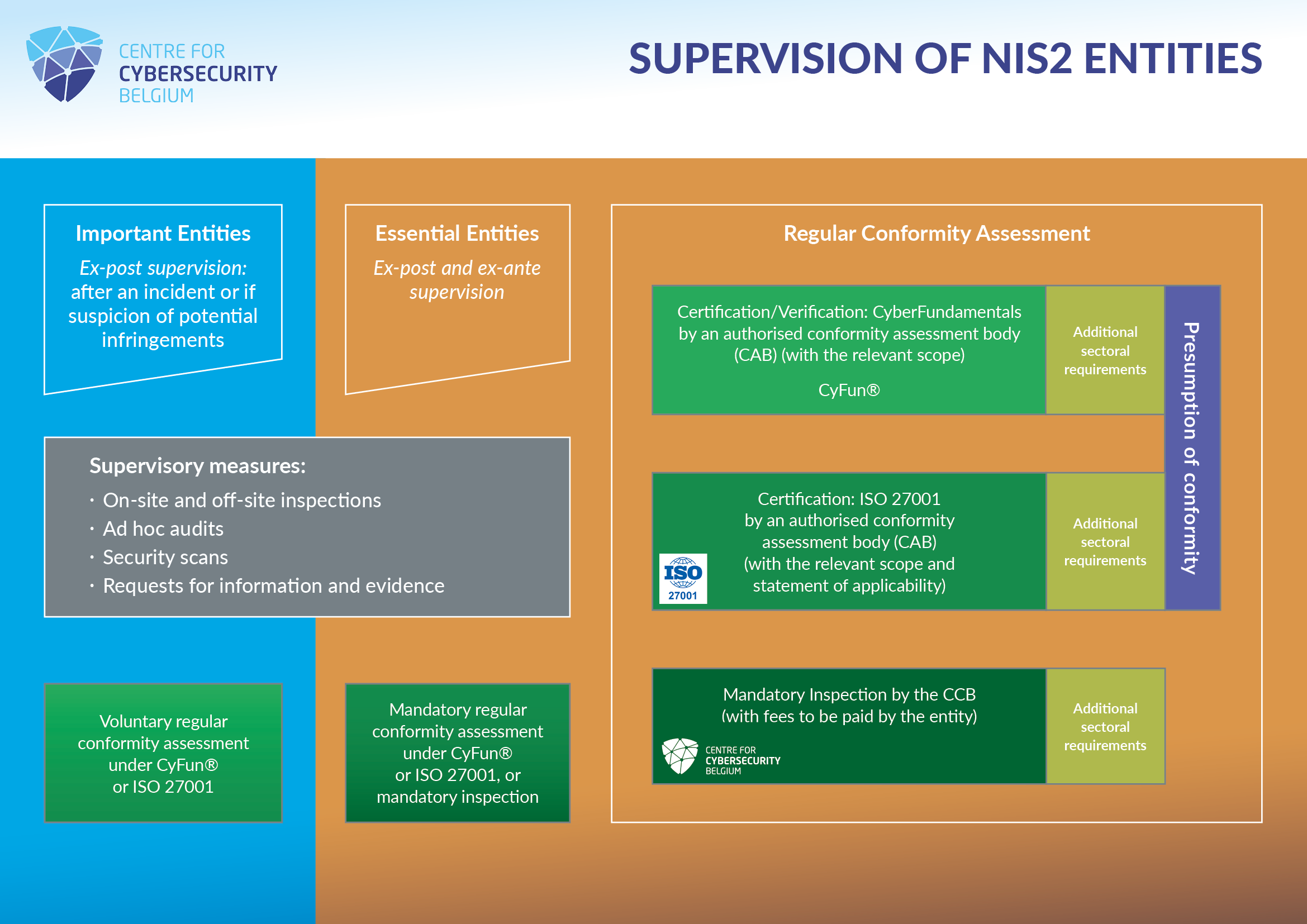
During its control, the CCB’s inspection service (or a sectoral inspection service, or both jointly) may have recourse to on-site inspections, off-site supervision, ad hoc audits, but also security scans and general requests for information and evidence. All NIS2 entities must at all times comply with the requests made by the inspection service(s). If they do not, they expose themselves to administrative fines.
Essential and important entities also have the possibility to use a CyFun® assurance level that is inferior to their NIS2 classification. For example, an essential entity could, based on a throughout risk-analysis, justify the use of the CyFun® level “Important”. This choice would be without prejudice to its classification as an essential entity under the NIS2 law. It should be noted that the inspection service may sanction an entity for wrongly conforming to a lower CyFun® level.
Inspectors will be able to go on site, take minutes and write reports. On the basis of these findings, a procedure may be initiated to order an entity to put an end to a violation and, if necessary, to take the appropriate administrative measures, ranging from warnings to administrative fines.
Potential administrative measures and fines are imposed by the Directive. If a measure or fine is deemed necessary, the situation and any repeated offences are always de facto taken into account so that the measure or fine taken is proportionate.
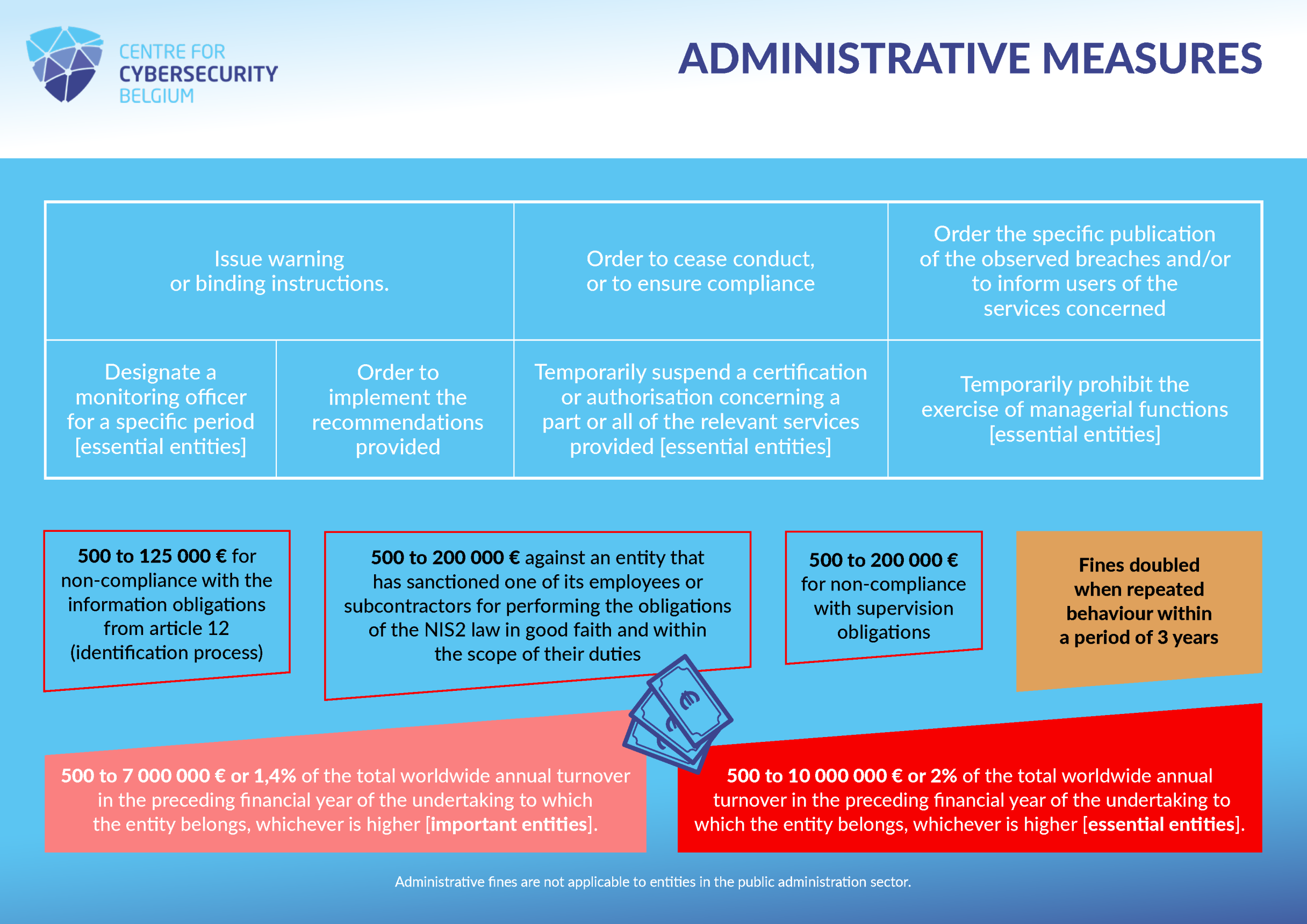
The following administrative fines can be imposed (doubled when repeated behaviour within a period of 3 years):
The CCB may also impose the following administrative measures:
The ultimate aim of these measures and fines is to strengthen the level of cybersecurity of essential and important entities and as such also the level of cybersecurity of the whole country.
Most obligations contained in the NIS2 legal framework are applicable from the 18th of October 2024. However, for some of them the law or the royal decree give entities an additional deadline before they must be applied.
Starting from 18th October 2024, notably the following obligations apply:
Concerning the registration of entities at the CCB via Safeonweb@Work, the law provides the following deadlines:
The supervision/regular conformity assessment of essential entities also takes a gradual approach:
More information about what NIS2 entities have to provide to the CCB by the deadlines specified above is available on the CyberFundamentals FAQ page.
The Centre for Cybersecurity Belgium created a comprehensive timeline for obligations and supervision applicable to essential and important entities:
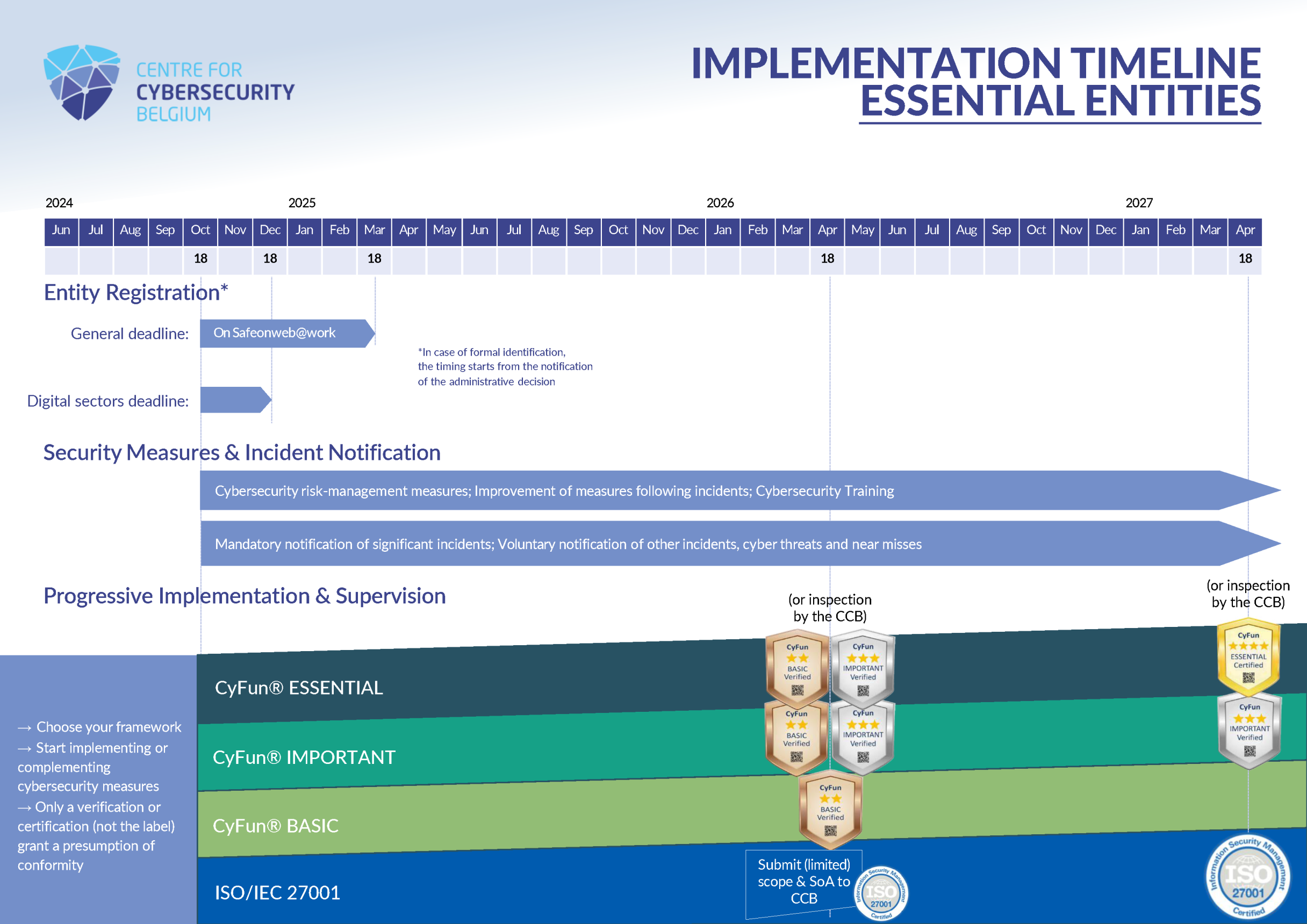
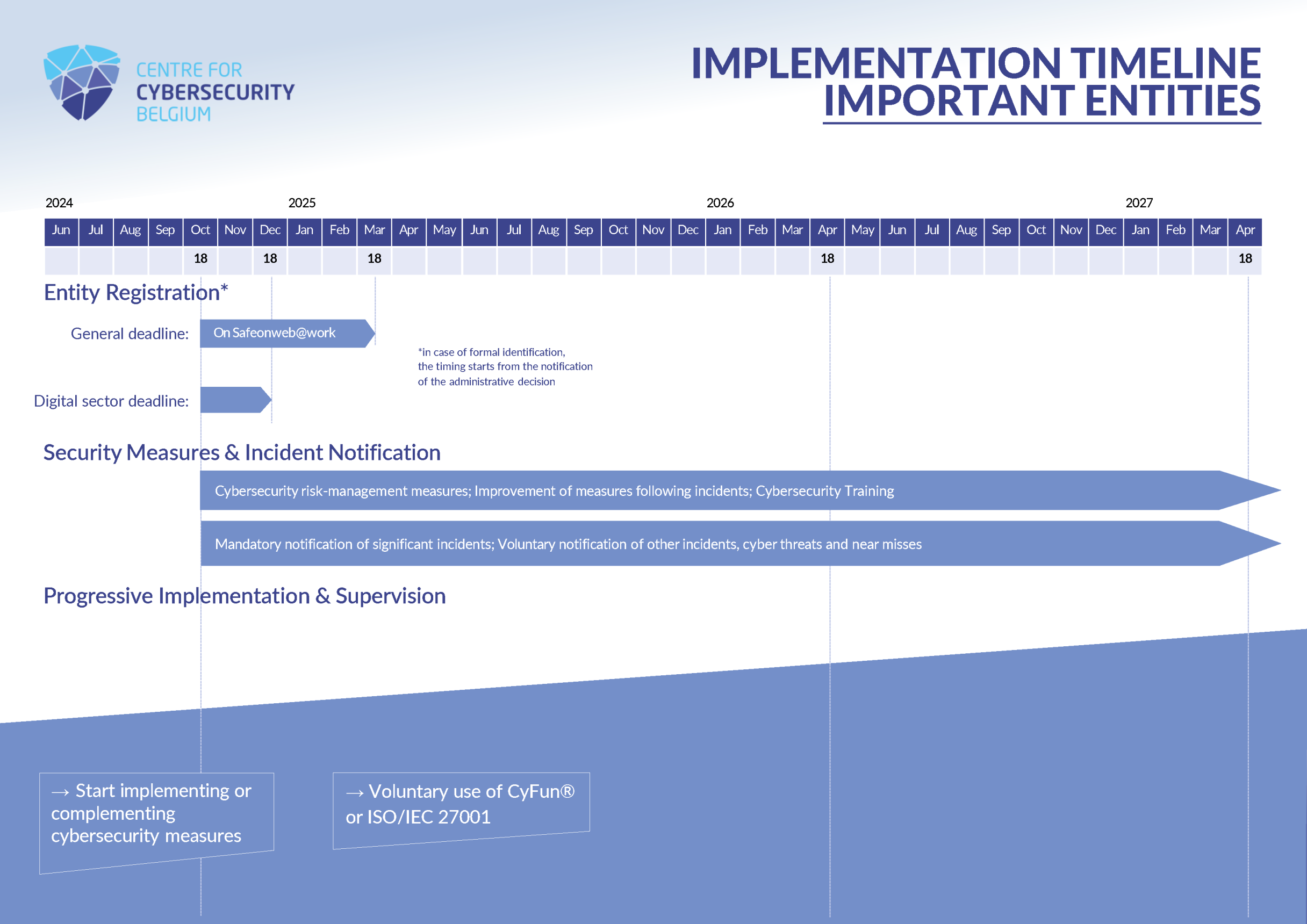
The Centre for Cybersecurity Belgium published an FAQ with contains a lot of further explanations on the NIS2 law. It may also be updated in the future to cover more questions.
More information on NIS2 is also available on the website of the CCB.
Beyond NIS2, the page on the CyberFundamentals Framework is also very useful.
Disclaimer: this page only contains information of general nature, provided by the CCB to the public about NIS2. It is not necessarily complete, exhaustive, accurate, or up-to-date, and does not constitute official advice by the CCB.
Only the texts published in the Belgian official journal are authoritative: see the law and the royal decree.